In September 2019, we started a dataset of Critical Infrastructures Ransomware Attacks (CIRAs). These are based on publicly disclosed incidents in the media or security reports. This dataset (version 12.9) now has 1,654 records assembled from publicly disclosed incidents between November 2013 and November 30, 2023, and has been mapped to the MITRE ATT&CK Framework. To date, we have fulfilled 1,489 requests.
If you use the dataset, in whole or in part, for any analysis, publication, presentation, or any other dissemination (including social media), you agree to cite this dataset in your reference list as:
Rege, A. (2023). “Critical Infrastructure Ransomware Attacks (CIRA) Dataset”. Version 12.9. Temple University. Online at https://sites.temple.edu/care/cira/. ORCID: 0000-0002-6396-1066.
PLEASE NOTE THE FOLLOWING:
- We do NOT send the dataset to a personal email (gmail, protonmail, hotmail, etc.). Allow 2-4 weeks for us to respond to your request.
- This dataset is free and accessible to the community. It can be used for educational/training purposes, conducting your own analysis/threat intel, sharing with stakeholders, etc. This limited license for the use of the dataset does not include commercial or for-profit purposes. Please do NOT use/share this dataset to develop commercial products/services/software that others have to pay for!
- By using this dataset you agree that all copyright and/or other proprietary notices on these materials must be kept intact and may not be removed.
The dataset will not be available for request from December 15th, 2023 – early/mid August 2024 as our Director is on sabbatical. We will still be working on it behind the scenes.
Want to submit a CIRA? Your contribution, if relevant, will be added to this dataset!
Our dataset has been featured in Security Week, Gartner, BRINK, Security Magazine, SentinelOne, Bleeping Computer, Dark Reading, Cyber Peace Institute, the Washington Post, Bloomberg, USA Today, Institute for New Economic Thinking, The Dallas Morning News, Business Insider, California News Times, Financial Times, CIO Dive, and eSecurity Planet!
To learn how we developed the CIRA dataset in greater detail, you can read our paper: Rege, A. & Bleiman, R.(2022) . “A Free and Community-driven Critical Infrastructure Ransomware Dataset”. Proceedings from the IEEE Cyber Science Conference.
| Summary Findings (2013-current) Most targeted CI: Government facilities Most common RW strain: Maze Most typical duration of RWAs: 1 week or less Most typical ransom amount demanded: USD 50,000 or lessDownload the 1-page summary |
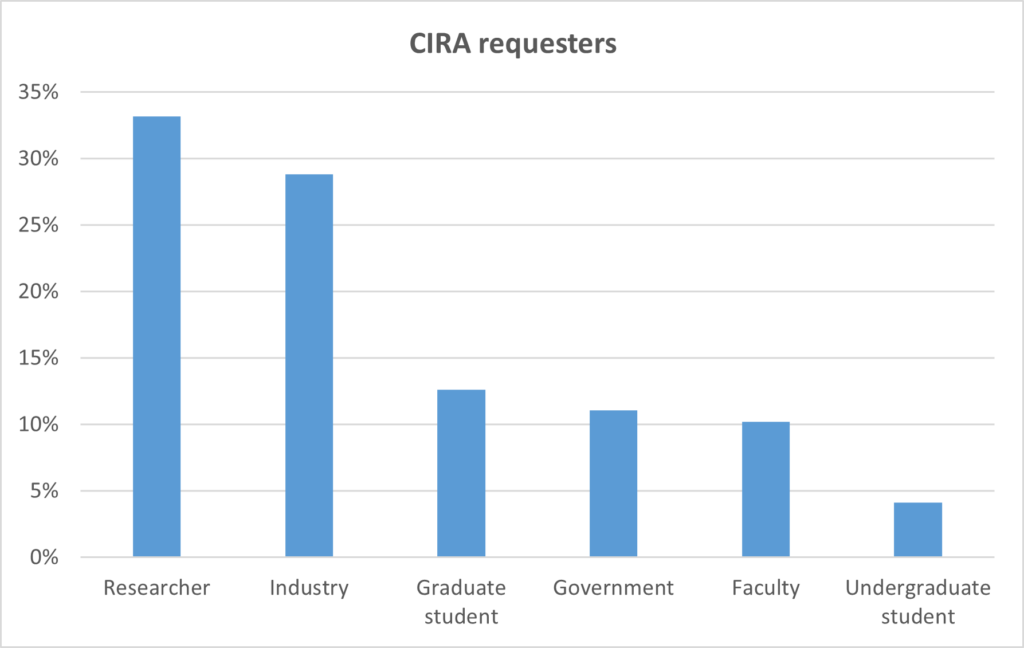
Who has requested our repository?
We have had download requests from government, industry, researchers, media, faculty, graduate and undergraduate students |
Check out these fantastic resources for ICS security.
var sc_project=12360776;
var sc_invisible=1;
var sc_security=”ddf74f40″;